Today I'm gonna talk about USB Drives.
I'll show you a simple trick to lock your USB drive without using any 3rd party software.
Most of the people doesn't like other people checking their personal files and folder on USB, including me. This insecure situation creates a huge space to theft our personal data by someone. If you use password protection to your USB, you can reduce the data theft.
Lots of USB password protect software available in present market, but you want to pay money to use it for lifetime. If you're using Windows you don't need any software.
So let's see how to set a password protect on your USB without using any software.
Insert your USB drive to computer
Click on Start
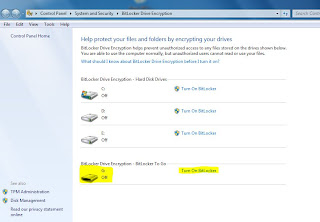
In "Search programs and files" box, type Bitlocker Drive Encryption
Now launch that application.
Then look for your USB drive and click on Turn on Bitlocker
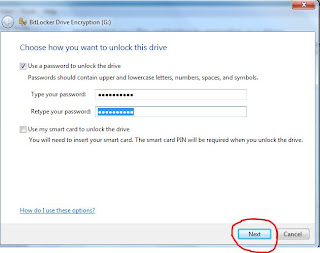
Windows will ask you to set a password.
Now set a strong password.
Most of the people doesn't like other people checking their personal files and folder on USB, including me. This insecure situation creates a huge space to theft our personal data by someone. If you use password protection to your USB, you can reduce the data theft.
Lots of USB password protect software available in present market, but you want to pay money to use it for lifetime. If you're using Windows you don't need any software.
So let's see how to set a password protect on your USB without using any software.
Insert your USB drive to computer
Click on Start
In "Search programs and files" box, type Bitlocker Drive Encryption
Now launch that application.
Then look for your USB drive and click on Turn on Bitlocker
Windows will ask you to set a password.
Now set a strong password.